Encryption and Hashing
In this section, we will take a look at two concepts which are widely used in Computer security.
Encryption:
Encryption is a cryptographic operation which transforms a text to a seemingly jumbled or a random text and decryption is an operation of retrieving the original text from the encrypted text.
There are two popular Encryption techniques:
- Symmetric key Encryption In this technique, the key used for encryption and decryption are the same.
- Asymmetric key Encryption (Public/Private Keys) In this technique, a different key is used for encryption and decryption. Generally, the encryption key is made public (hence the name) and the decryption key (private key) is held privately by the encrypter. Note that, specific algorithms are available to generate a set of Public and Private Keys.
Importance of Public/Private Keys:
Public/Private Keys are used in a variety of applications, the most important being to secure message transmission. In general, this concept (as defined below) is used in implementing transport layer security (e.g., HTTPS), PGP etc.
Use of Encryption in secure message transmission:
In message transmission, public/private key encryption is generally used. The receiver of the message would generate a set of public/private keys and would make the public key known to everyone (so anybody can encrypt and send messages) and the decryption key is held securely with itself. Thus, when a message has to be relayed to the receiver, the sender would encrypt the message using public key. The receiver would decrypt the message using private key.
Below is a list of algorithms which provide Public/Private key cryptography:
- RSA
- Digital Signature Algorithm
Hashing:
Hashing is a mathematical operation which transforms a text or a set of characters into a different text or set of characters. The mathematical function which performs this operations is known as a Hash function. The result of a hash operation is known as a hash result or just ‘Hash’ value.
An ideal hash operation is irreversible. i.e., we cannot derive the original text by operating on the hash result.
Salt:
Salt is a random data that is used as an additional input to the hash function. It would help in generating hashes which are difficult to guess or reverse engineer the hash to retrieve the original text.
Importance of hash in security:
In the software security world, hash plays an important role as illustrated below.
1. Securing message communication against tampering the message in between:
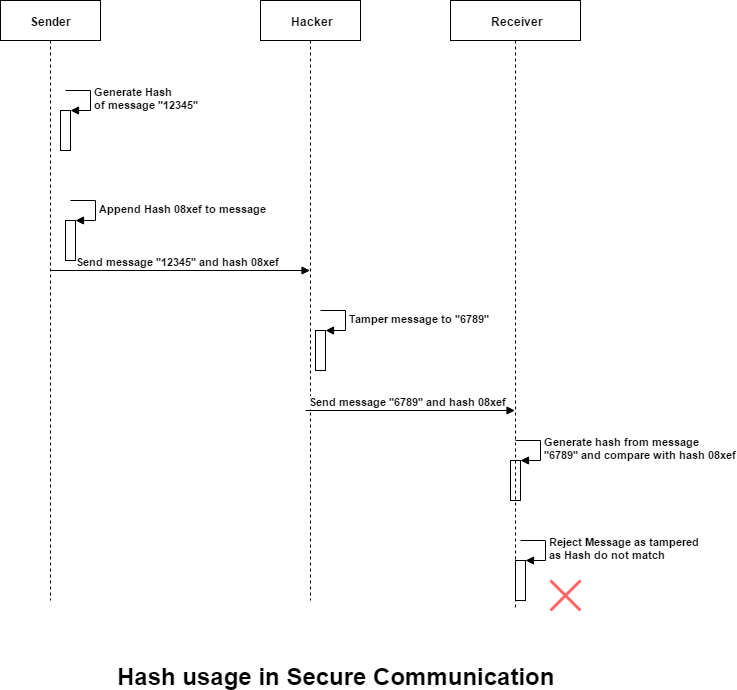
Let us say system A is sending a message to system B by some means (like HTTP communication). A hacker can intercept the transmission in between and tamper the message. In order to prevent this scenario, the hash could be used in the following way.
- The sender would generate a hash of the message using a secure key which is only known to the sender and the receiver.
- The sender would send the message as well as the hash to the receiver.
- The receiver would retrieve the message and the hash. The receiver would generate its own hash from the message and the key (which was agreed upon between sender and receiver).
- The receiver would compare the hash which it generated in step c with the hash sent by the sender. If both of them match, then the receiver can conclude that the message has not been tampered with. If the hashes do not match, then the message has been tampered with.
Since, the hacker will not know about the secret key required while generating the hash, the message cannot be tampered with, or else the receiver would come to know about it.
2. To store passwords for authentication:
Generally, application user passwords were being stored in an encrypted format. However, with the advance in technology, it is becoming far easier for powerful systems to decrypt the encrypted passwords. Thus, if a hacker gets hold of the database having encrypted passwords, then decrypting them would lead to compromising secure accounts. To overcome this, hashing is generally used.
- The password is first hashed and the resulting hash is then encrypted and stored in database.
- Even if a hacker gets hold of the encrypted value and decrypts it, the hacker cannot retrieve the original text from the hash.
- During login, when a user provides username/password for authentication, the system would first decrypt the value from database and retrieve the hash. The system would then compare the hash of the password provided by the user and the hash retrieved from the database. If they match, the authentication is considered successful. Note that in this setup, there is no way to retrieve the original password from the system.
The popular hash functions used in security include:
- MD2
- MD4
- MD5
- Secure Hash Algorithm (SHA-1, SHA-2)
Generally, Secure Hash Algorithms (SHA-1/SHA-2) along with a random salt are used to hash passwords and store it in database. Note that the salt should be randomly generated and should be different for each user and stored along with the hash in the database. Creating a random salt per user would add additional security and guard against rainbow table attacks.