SAML
In this section, we will take a look at SAML, which is a popular security protocol, used very widely.
Security Assertion Markup Language (SAML) is an XML-based, open-standard data format for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. SAML is a product of the OASIS Security Services Technical Committee.
SAML is generally used in implementing Single Sign On. Single Sign On is generally used in intranet applications in a corporate network, wherein, a user can login to a single application and navigate to other applications seamlessly without having to login to each application
SAML Concepts:
- Identity Provider (Idp)
- Service Provider (SP)
- Principal
- Assertions
1. Identity Provider (Idp):
An Idp, maintains a list of valid users of the system and provides a service to authenticate an user. This process of authentication is generally termed as ‘Assertion’. As part of the assertion, the Idp also provides information it has about the user (or the principal). An Idp also provides a service which validates the authenticity and the validity of a token.
2. Service Provider (SP):
A SP, provides the actual service (or is the application) which would be used by end users.
3. Principal:
Principal is the actual end user or a client system (who provides credential for authentication) and consumes the services provided by the Service Provider.
4. Assertions
Assertions are packets of security information exchanged between Identity Provider and Security Providers.
SAML is generally built upon XML and SOAP specifications and exchange of information happens through digitally signed XML documents, thereby making it secure.
SAML Flows:
There are two common flows associated with SAML.
- SP initiated SSO
- Idp initiated SSO
A common step is to have the Identity Provider and Service Providers establish themselves and this process is known as Provisioning. This is a one-time activity.
Login Scenarios:
The below diagram illustrates SP Initiated flow for simplicity.
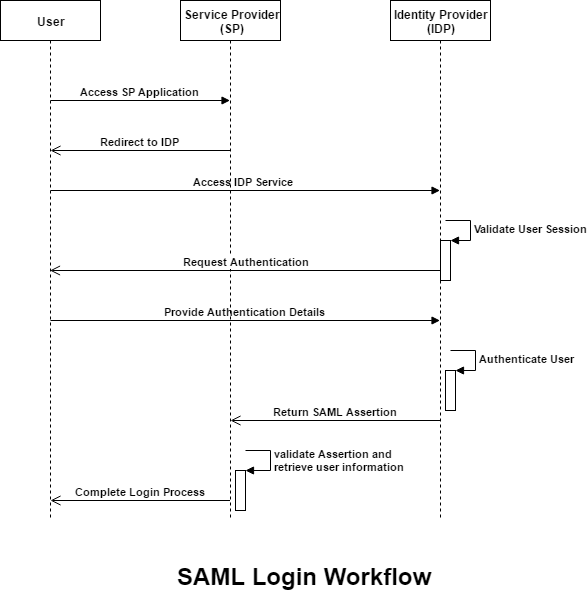
1. SP initiated SSO:
- A user clicks on an application link which is rendered by a Service Provider.
- The SP application redirects the user to an Identity Provider, asking for authentication.
- The Identity Provider, checks if a valid session for the user has already been created and is active. a. If there is no such session, the Idp asks the user to authenticate. After successful authentication, the Idp creates a session and returns a SAML assertion with the user details. b. If a valid session is already created, then the Idp returns a SAML assertion with the user details.
- The SP receives the authentication assertion from the Idp and validates the response.
- The SP allows the user to access its services.
2. Idp initiated SSO:
- A user clicks on a portal page which is rendered by the Identity Provider.
- The Identity Provider, checks if a valid session for the user has already been created and is active. a. If there is no such session, the Idp asks the user to authenticate. After successful authentication, the Idp creates a session and returns a SAML assertion with the user details. b. If a valid session is already created, then the Idp returns a SAML assertion with the user details.
- The authenticated user then clicks on any of the links provided by the SP.
- The SP receives the authentication assertion from the Idp and validates the response.
- The SP allows the user to access its services.
So, in general, Idp initiated SSO is used if the user lands on a well-defined login or portal page and then moves on to access any of the links provided by the SP. SP initiated SSO is used, if the user clicks on any of the deep links provided by the SP (without going through the initial portal login page).
Logout Scenarios:
SAML also supports logout scenarios from multiple applications as explained below. The below examples correspond to a web SSO application flow.
1. SP initiated Logout:
- A user, who is logged into a SP, clicks on a logout button.
- The SP terminates the session and initiates a logout request to the Idp.
- The Idp finds out how many SP sessions are maintained by it.
- If there is only one SP (the one which initiated logut), then it sends back a logout response.
- If there are other SPs whose session is valid, then the Idp sends out a logout request to each of the SPs.
- The SPs respond back with a logout response.
- The Idp terminates the session maintained by it for this user and sends a logout response to the SP who initiated the logout request.
2. Idp initiated Logout:
The Idp initiated logout scenario is similar to the above, except that it starts from step 3. It would be initiated when the user clicks on a global logout link provided in the portal or if the Idp session expires.
Reference Use cases:
SAML is used in implementing Single Sign on, for related applications. A common use case is Single Sign on for Employee related applications in a corporate, like Leave management system, Employee Profile application etc.